ShmooCon 2008 Tickets - Round Two
If you are planning on going to ShmooCon next year (February 15-17, 2008 in Washington, DC) and haven't already acquired your tickets, the 2nd round of ticket sales is December 1st (tomorrow) at Noon EST.
If the 2nd round is anything like last year (actually this year on 1/1), it will be insane. The Early Bird tickets were completely gone in the first five minutes. I jumped in the fray as soon as registration opened and by the time I was done entering my info, there were only four Early Bird tickets remaining. Anybody that was still sleeping off their hangover from the night before or in the least bit groggy missed out. Some people also had their tickets sold out from under them while they entered the credit card data. They thought they were getting a $75 ticket but ended up with $150 one.
Well this year, the ShmooCon ticket sales have been updated to address the situation. Now one of each type of ticket is reserved for five minutes after the order process is started. Apparently the number that you can purchase are still unlimited, which means that some strategy is required to get the type of ticket you want. If you haven't started the order process before a multiple ticket purchaser completes the process, you will miss out. So unless you want to end up like a whiny preteen rolling the dice on eBay, make sure you are within the first 250 people as soon as ticket registration opens (and that would be the first 100 for you cheapskates looking for $75 tickets).
What if you are gunning for the $300 "I Love ShmooCon" ticket (because you really, really want that free T-Shirt). Paradoxically, you need to be within the first 10 people to start the order process. Since one type of ticket is reserved for each person, the hordes of people trying to get Early Bird or General Admission tickets quickly exhaust the supply of available "I Love ShmooCon" tickets. This is further aggravated as the other types of tickets are sold out and people repeatedly refresh the order process to see if any previously reserved tickets are added back to the pool.
So, what should you do to make sure that you can get the "I
Love ShmooCon" ticket? Start the order process early. Really
early. Like 11:55 AM early. Because there is currently a time
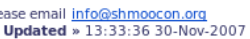
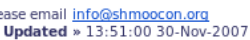
skew of five minutes on the registration server. This is easily
noticeable from the fact that the time at the bottom of the registration page is dynamically updated when the page is
refreshed:
And since hammering on the registration page is pretty lame, why not use a simple shell script instead:
#!/bin/sh
host=www.shmoocon.org
echo "$host/cart/ "`printf "HEAD /cart/ HTTP/1.0\r\nHost: $host\r\n\r\n" | openssl s_client -connect $host:443 -quiet 2>/dev/null | grep ^Date`
echo "my date: `date -u`"
# eof
Who knows how long this might last, but it was that way on November 1. By looking for a slight competitive advantage, you can be sure to get in early and get your coveted "I Love ShmooCon" ticket before they are all gone.
Personally, I made sure to get my ticket on November 1st to avoid all the craziness. Even then, Early Bird tickets probably only lasted twenty minutes. But I may just stop by this time just to see how frenzied the action is.
If you are on the fence about going, ShmooCon is definitely worth it. Go to ShmooCon.