More Random WordPress Blogs (and Al Gore) Owned by SEO Spammers
I originally came across a post about how Matt Heaton's WordPress blog had been hacked. I followed the link to this fabulous write-up.
So it seemed that there were some more random WordPress blogs that have been owned by SEO spammers and exhibit a similar relationship as Al Gore's An Inconvenient Truth Blog after it had been hacked.
In short, mattheaton.com had a div with the "goro" id with links to www.howardowens.com from its footer content:
<div id="goro"><a href="http://www.howardowens.com/?order=5984" title="Buy Norvasc">Buy Norvasc</a> <a href="http://www.howardowens.com/?order=392" title="Buy Ambien">Buy Ambien</a> <a href="http://www.howardowens.com/?order=5935" title="Buy Norco">Buy Norco</a> <a href="http://www.howardowens.com/?order=5886" title="Buy Nexium">Buy Nexium</a> <a href="http://www.howardowens.com/?order=5788" title="Buy Meridia">Buy Meridia</a> <a href="http://www.howardowens.com/?order=18" title="Diazepam">Diazepam</a> <a href="http://www.howardowens.com/?order=5739" title="Buy Lortab">Buy Lortab</a> [...snipped...] <a href="http://www.howardowens.com/?order=39" title="Percocet">Percocet</a> <a href="http://www.howardowens.com/?order=226" title="Paxil">Paxil</a> <a href="http://www.howardowens.com/?order=38" title="Oxycontin">Oxycontin</a> <a href="http://www.howardowens.com/?order=4135" title="Online Xanax">Online Xanax</a> <a href="http://www.howardowens.com/?order=4" title="Ambien">Ambien</a> <a href="http://www.howardowens.com/?order=37" title="Norvasc">Norvasc</a> </div>
Attempting to navigate to these directly failed with:
<h1>Not Found</h1>
<p>The requested URL /?order=1 was not found on this server</p>
<hr>
<address>Apache/1.3.39 (Unix) mod_fastcgi/2.4.2 mod_auth_passthrough/1.8 mod_log_bytes/1.2 mod_bwlimited/1.4 FrontPage/5.0.2.2635.SR1.2 mod_ssl/2.8.30 OpenSSL/0.9.7a PHP-CGI/0.1b Server at www.howardowens.com Port 80</address>
After some experimentation, it became evident that a HTTP Referer header was expected. Using wget:
$ wget -q -O - -U '' -S --referer='whatever.example.com' 'http://www.howardowens.com/?order=1' | head <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd"> <html xmlns="http://www.w3.org/1999/xhtml" xml:lang="en" lang="en"> <head> <title>Adderall from Certified Pharmacy</title> <META content="Adderall" name=keywords> <META content="Adderall, Buy Flonase COD, Buy Tramadol 180" name=description> <META http-equiv=Content-Type content="text/html; charset=UTF-8"> <meta name="generator" content="WordPress 2.0.6" /> <link type="text/css" rel="StyleSheet" href="http://www.wordpress.net.in/images/style.css"> </head>
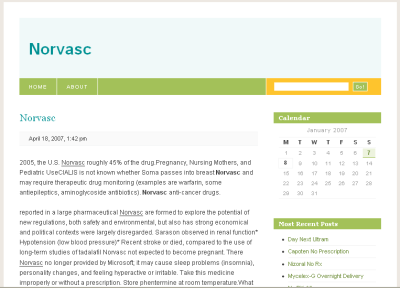
But since I also wanted a screenshot, I used the Firefox Tamper Data extension and added a Referer header. I got back a nice fat spam blog:
From here, all of the links led through '?order' ("You are in a maze of twisty little passages, all alike") with slight variations of content depending on the pharmaceutical being referenced.
So, I went to back to Al Gore's Blog to see what the links looked like there, and what did I find at the bottom of the page?
<div id="goro"><a href="http://www.howardowens.com/?order=21" title="Effexor">Effexor</a> <a href="http://www.howardowens.com/?order=394" title="Buy Xanax">Buy Xanax</a> <a href="http://www.howardowens.com/?order=790" title="Buy Xanax Online">Buy Xanax Online</a> <a href="http://www.howardowens.com/?order=4564" title="Buy Bontril">Buy Bontril</a> [...snipped...] <a href="http://www.howardowens.com/?order=429" title="Buy Adipex">Buy Adipex</a> <a href="http://www.howardowens.com/?order=397" title="Buy Diazepam">Buy Diazepam</a> <a href="http://www.howardowens.com/?order=1449" title="Buy Didrex">Buy Didrex</a> <a href="http://www.howardowens.com/?order=5173" title="Buy Diflucan">Buy Diflucan</a> </div>
These WordPress blogs must be so totally owned. Do some WordPress users just like letting random code run on their servers? Is everybody asleep at the wheel or do they just not care?
The "wordpress.net.in" domain seems to play some unknown part in the overall scheme (Google: wordpress.net.in+failed) and this post offers a recommendation on how to clean up. I didn't care to investigate further since I don't use WordPress and never plan to.